Tackling Web Exploitation Challenges
This year I participated in MagpieCTF 2025, which hosted many challenges including a web exploitation challenge called Cops Like Ciphers and Cookies. Before I attempted it, my teammate (credit to him) and I completed a couple of other web exploitation challenges prior to this and they all involved cookie tampering, so I decided to narrow the possible attack vectors to that area and follow the KISS principle (Keep it simple, stupid).
1. Initial Enumeration
1.1 Landing page
In web exploitation, its important to follow a methodology in order to be successful. I always start out my viewing the page as if I was a normal user.
Make detailed observations on your findings because everything is created with a purpose. When I found something I didn't understand, I would ask myself:
What is the purpose of this? Why is this here? Can I take advantage of it?
If there's anything you find that you don't understand, you need to keep enumerating. The hardest part of web exploitation isn't exploitation, but rather it's enumeration.
When visiting the site, I was greeted with the following landing page:
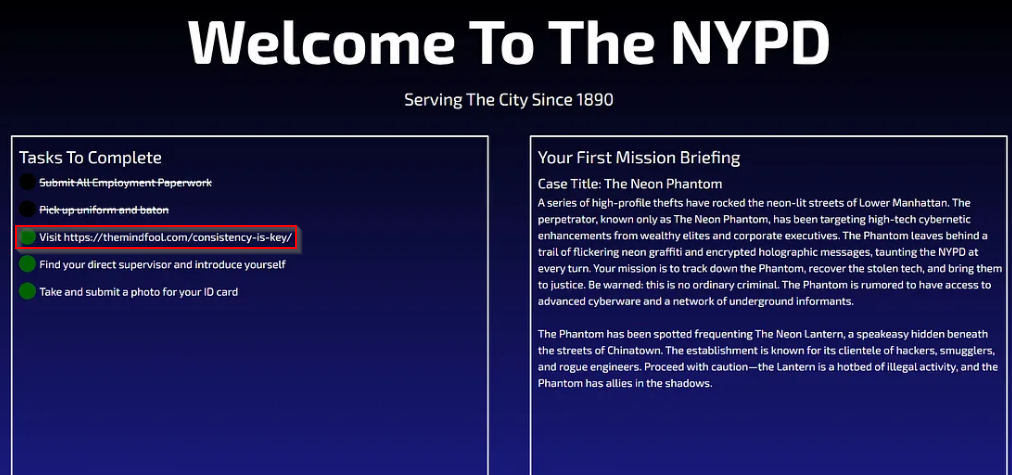
Upon first glance, nothing really sticks out and just looks like a normal static landing page. However, after reading its contents, one sentence sticked out like a sore thumb. Given the content written on the landing page, the checklist entry saying Visit https://themindfool.com/consistency-is-key didn't seem to match when given the context of the page. I made sure to keep a mental note of that as it seemed to be the first puzzle piece for finding the solution.
It's always important to make sure to look at the source code as well. After not making any further discoveries from viewing the landing page, it was time to look at what there was under the hood to see what was hiding from the naked eye:
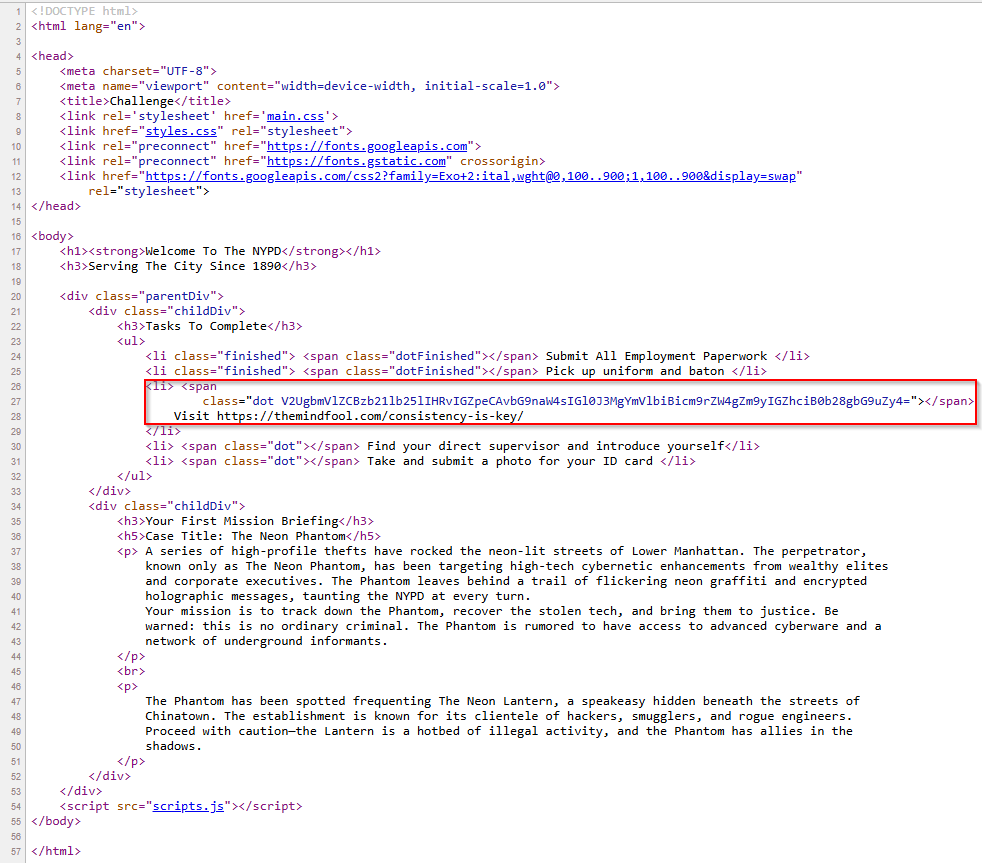
With the initial observation I made on the landing page with Visit https://themindfool.com/consistency-is-key, I made sure to check that first. I noticed a long string of characters in the class attribute for it which was also ringing alarm bells. I didn't understand the purpose of it and why it was there, which means I won't know how to take advantage of it. Given the fact that no other class attribute was like that, I decided that identifying what that string represented was my first step.
I saw that the string ended with =, which is an indication of a possible base64 encoded text. To follow up with my hypothesis, I decided to do a quick check.
In a Linux terminal:
echo V2UgbmVlZCBzb21lb25lIHRvIGZpeCAvbG9naW4sIGl0J3MgYmVlbiBicm9rZW4gZm9yIGZhciB0b28gbG9uZy4= | base64 -d
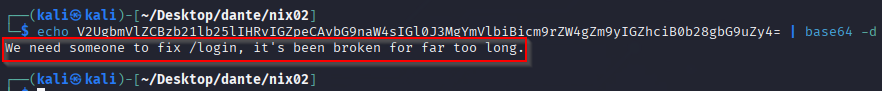
From the output, we now have another directory to investigate!
1.2 Login page
Navigating over to /login, we follow the same starting steps as before:
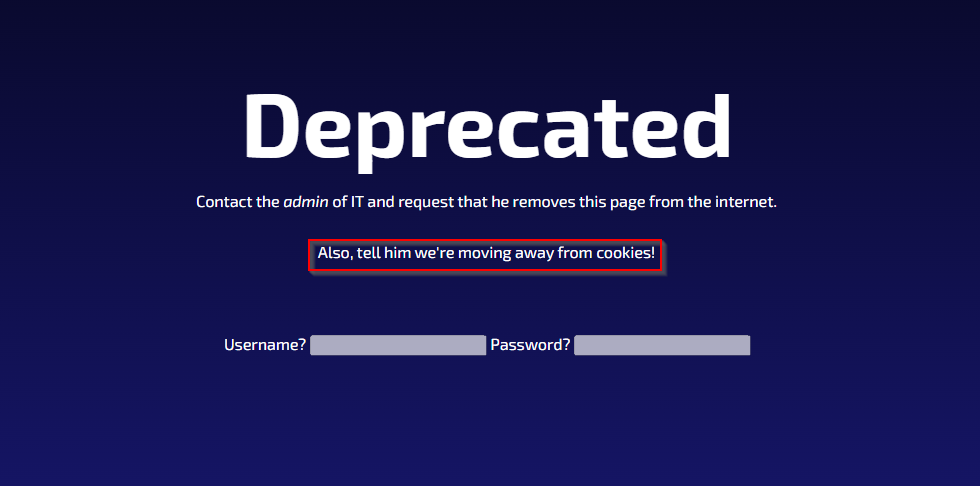
It looks like a normal log in page, except with one big difference. The username and password fields are both blocked and preventing input. However, based on the hint Also, tell him we're moving away from cookies! and the fact that the theme has been cookie tampering throughout the challenges, I decided to investigate the input fields as a last resort since it didn't seem connected to the challenge.
Moving onto the source code (I lost the screenshot), I found something similar to what I found on the landing page. <meta name="description" content="dmlnZW5lcmU="> was hidden within the code to not appear on the /login page. The string in content has an interesting string that appears to be random. My first instinct was to decode it since it's most likely to be base64 encoded as well.
In a Linux terminal:
echo dmlnZW5lcmU= | base64 -d
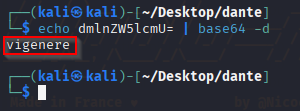
With the output being vingenere, something I've never heard of before, I did what any normal person would do...
Google:
Now, I know this has something to do with encryption, but I'm still missing the last puzzle piece. The login cookie.
Opening burpsuite, I turn on the proxy in order to analyze the traffic going through my browser. I refresh the page with intercept on, and sure enough, I catch the Cookie field in the HTTP request.
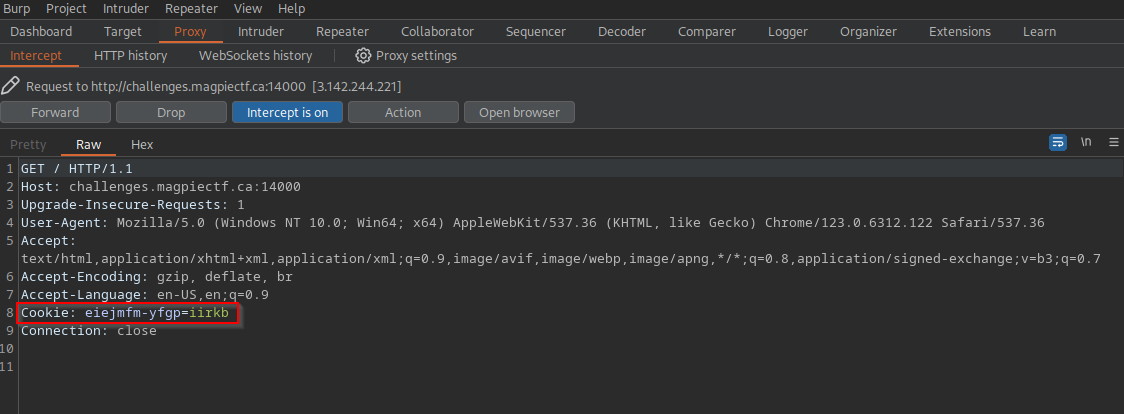
The cookie appears to have a random value on the surface, but given the privious finding of vingenere cipher, I know that this cookie has to be decrypted. All that's left is connecting the dots from the findings. Since vingenere is a symmetric algorithm that requires a key in order to encrypt and decrypt, I just had to find that key in order to change the cookie so that we become authenticated users. Thinking back landing page, I remembered the website https://themindfool.com/consistency-is-key and that's when everything clicked. The key to the vingenere cipher is consistency.
2. Exploitation
2.1 Cookie Tampering
Now that we have all the information needed, we can proceed with exploiting it in burpsuite. Using the key consistency on the cookie eiejmfm-yfgp=iirkb we end up getting current-user=guest. Now let's try changing guest to admin and sending it.
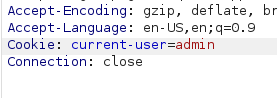
However, this ended up failing. Now let's try encrypting it again with the same key and sending it.
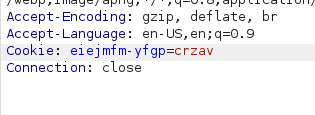
And just like that we completed the challenge. gg